4.3
7 votos
|
Seguir (516 )
Rss
Información
Autor (es):
Robert Kirkman y Joe Keatinge
Artista:
Dave McCaig, Khary Randolph
Idioma:
Español
Enviar
Enviar mensaje
 |
NiallHiryk
Aug 20, 2018
|
#Boku-no-Hero-Senti um pouco de vergonha alheia na parte em que ele bate no monstro e quis parar, mas fiquei realmente feliz por não telo feito pós é realmente bom e entendi porque ficou popular em 2014.
|
|
Heber
Dec 21, 2022
|
Vintage Jackets Mens
Vintage jackets for men are the perfect way to add a touch of style to any wardrobe. Whether you are looking for a classic leather bomber jacket or a more modern style, there is something to suit every taste. From timeless tweed jackets to more modern nylon styles, you will find a variety of styles and fabrics to choose from. Whether you are looking for a lightweight option to keep you warm in the springtime or a heavier jacket for winter, you can find the perfect vintage jacket for men.
Click Here for this Amazing Jacket and much more. https://www.jacketars.com/product/mens-retro-red-waxed-vintage-jacket/
Vintage jackets for men are the perfect way to add a touch of style to any wardrobe. Whether you are looking for a classic leather bomber jacket or a more modern style, there is something to suit every taste. From timeless tweed jackets to more modern nylon styles, you will find a variety of styles and fabrics to choose from. Whether you are looking for a lightweight option to keep you warm in the springtime or a heavier jacket for winter, you can find the perfect vintage jacket for men.
Click Here for this Amazing Jacket and much more. https://www.jacketars.com/product/mens-retro-red-waxed-vintage-jacket/
|
|
lisacarol864
Feb 03, 2023
|
if you are looking for a 70's Show Outfit so you can visit us :https://www.theamericanoutfit.com/product/danny-masterson-that-70s-show-stuntman-jacket/
|
|
lateenprank
Dec 21, 2022
|
Vintage jackets for men are an excellent way to add a stylish touch to any wardrobe. There is something to suit every taste, whether you want a classic leather bomber jacket or a more modern version.
https://idlebreakout.io
https://idlebreakout.io
 |
charlotte jackson
Dec 28, 2022
|
https://www.theamericanoutfit.com/product/cole-hauser-yellowstone-rip-wheeler-black-cotton-jacket/ is here to clear the dilemma of fashionable dressing once and for all. This website holds jackets and coats made from genuine leather and premium quality fabric to satisfy your craving for Movie, Video Game and TV Series-inspired attires. Best prices, at speediest delivery, only by The American Outfit!
 |
TresCatorce
Feb 06, 2019
|
Series que puede que no conozcas (3)
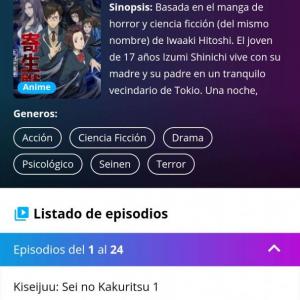
➡️Título⬅️: Kiseijuu (Parasyte)
📃Géneros📃: Ciencia ficción, horror, drama, misterio, acción.
Del cielo caen esporas. Al abrirse, liberan unas pequeñas criaturas con forma de gusanos que buscan carne viva donde alojarse. Una mañana Shinichi se despierta y siente su mano rara, hasta que esta empieza a hablar; el parásito se ha comido su mano derecha
Recomendación: 20/10. Mientras que el manga empezó en 1988, el anime salió en 2014-15, la diferencia de calidad se nota. La animación y la banda sonora es fantástica, te hace vivir las escenas de acción. No suelo decir esto pero no pasa nada si no leen el manga, pero DEBEN ver el anime. No se arrepentirán.
➡️Título⬅️: Kiseijuu (Parasyte)
📃Géneros📃: Ciencia ficción, horror, drama, misterio, acción.
Del cielo caen esporas. Al abrirse, liberan unas pequeñas criaturas con forma de gusanos que buscan carne viva donde alojarse. Una mañana Shinichi se despierta y siente su mano rara, hasta que esta empieza a hablar; el parásito se ha comido su mano derecha
Recomendación: 20/10. Mientras que el manga empezó en 1988, el anime salió en 2014-15, la diferencia de calidad se nota. La animación y la banda sonora es fantástica, te hace vivir las escenas de acción. No suelo decir esto pero no pasa nada si no leen el manga, pero DEBEN ver el anime. No se arrepentirán.
 |
Niko 7u7
Apr 06, 2019
|
#Manga y Anime Reviews ¶∆
Videojuego+Seinen+Muerte=Bl@ck⭐Out (matemáticas hijo.jpg)
Esta es una novela de Kuroi Ransuke que ha sido adaptada en manga por Maekawa Kazuo, tiene 3 volúmenes y fue publicada en 2014. Si bien la temática puede sonar sosa y repetitiva, y puede que te recuerde a alguna otra serie, lo cierto es que está contada de una manera excepcional, al principio puede que parezca como cualquier otra historia pero dale una oportunidad, estoy seguro que te dejará con ansias de más.
Una reciente ola de muertes con causa desconocida azota la ciudad de Kazuya Shibuya, un chico de 18 años desempleado y con dos únicos amigos, lleva una vida normal sumergida en la rutina, resignado a lo que le depare el futuro una noche llega a su casa un mensajero con un paquete a su nombre el cual contiene un juego llamado Bl@ck⭐Out el cual le ofrece ganar dinero real por jugar, el se deja llevar por el aburrimiento y entra al juego pero pronto se dará cuenta de que es más real de lo que parece.
Un seinen que te dejará enganchado.
Videojuego+Seinen+Muerte=Bl@ck⭐Out (matemáticas hijo.jpg)
Esta es una novela de Kuroi Ransuke que ha sido adaptada en manga por Maekawa Kazuo, tiene 3 volúmenes y fue publicada en 2014. Si bien la temática puede sonar sosa y repetitiva, y puede que te recuerde a alguna otra serie, lo cierto es que está contada de una manera excepcional, al principio puede que parezca como cualquier otra historia pero dale una oportunidad, estoy seguro que te dejará con ansias de más.
Una reciente ola de muertes con causa desconocida azota la ciudad de Kazuya Shibuya, un chico de 18 años desempleado y con dos únicos amigos, lleva una vida normal sumergida en la rutina, resignado a lo que le depare el futuro una noche llega a su casa un mensajero con un paquete a su nombre el cual contiene un juego llamado Bl@ck⭐Out el cual le ofrece ganar dinero real por jugar, el se deja llevar por el aburrimiento y entra al juego pero pronto se dará cuenta de que es más real de lo que parece.
Un seinen que te dejará enganchado.



|
|
hrish
Feb 21, 2023
|
Full Stack Development and Cloud Computing are two of the most exciting and rapidly evolving areas in the tech industry today. Understanding the benefits of these technologies is essential for anyone looking to stay ahead in the ever-changing world of tech.
In this article, we'll dive into the world of both these domains, exploring the benefits and considerations of these technologies, and discussing why they are becoming increasingly important in today's tech landscape. Whether you're a tech professional or simply a tech enthusiast, you're sure to learn something new and thought-provoking as we dive into this exciting topic!
What is Full Stack Development?
Full Stack Development refers to the practice of developing both the front-end and back-end components of an application. Full Stack Developers possess a broad range of technical skills and knowledge, allowing them to develop, maintain and manage all aspects of an application.
To be a Full Stack Developer, you need to have a strong understanding of front-end technologies like HTML, CSS, and JavaScript, as well as back-end technologies such as servers, databases, and APIs. These technologies work together to create a seamless user experience, from the way a website looks and feels to the way it processes and stores data.
The front-end, or client-side, of an application is responsible for the visual design and user interaction. The back-end, or server-side, is responsible for processing data and communicating with the front-end. Full Stack Developers must have a good understanding of both sides of the application to ensure that they are working together smoothly.
What is Cloud Computing
Cloud Computing refers to the delivery of computing services—including servers, storage, databases, networking, software, analytics, and intelligence—over the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale.
There are three main categories of cloud computing services:
● Infrastructure as a Service (IaaS): provides virtualized computing resources over the internet. This includes virtual machines, storage, and networking.
● Platform as a Service (PaaS): provides a platform for developing, running, and managing applications and services.
● Software as a Service (SaaS): provides access to software applications over the internet, without the need for installation or maintenance.
One of the biggest advantages of cloud computing is its scalability. You can easily scale your resources up or down depending on your needs, without having to invest in additional hardware. This means that you can quickly respond to changes in demand, without having to worry about the underlying infrastructure.
Benefits of Full Stack Development and Cloud Computing
These 2 fields are two of the most important technology trends in today's tech landscape. When combined, they bring a multitude of benefits that can enhance the development process, improve user experience, and save costs. Let's dive into some of the key benefits of cloud computing and full stack development.
A. Improved Collaboration and Communication
One of the biggest benefits of is improved collaboration and communication. With Full Stack Development, front-end and back-end developers work together seamlessly, leading to improved collaboration among teams. This also leads to better communication between developers and clients, as everyone is on the same page in terms of the development process.
B. Increased Flexibility and Scalability
Full Stack Development allows developers to be flexible in their development processes, allowing them to quickly pivot and make changes as needed. This is especially important in today's fast-paced tech landscape where projects can change quickly.
Cloud Computing also provides scalability, as applications can be easily scaled up or down based on the needs of the project. This means that as the demand for an application grows, it can be easily scaled to meet that demand, without having to worry about the costs associated with purchasing new hardware.
C. Reduced Costs
With cloud computing, organizations can reduce the costs of hardware and infrastructure, as well as the costs associated with maintenance and updates. This is because it allows organizations to pay for only what they use, rather than having to purchase and maintain their own hardware.
D. Improved Security
Security is a major concern for organizations in today's tech landscape, and full stack development and cloud computing can help improve security measures. Cloud computing provides enhanced security measures, such as encryption and data backup, to protect sensitive information. Further, full stack development can improve data protection, as developers can build security measures at every stage of the development process.
E. Better User Experience
Both these tech fields can also lead to a better user experience. With full stack development, developers can create applications with enhanced functionality, which can greatly improve the user experience. Also, cloud computing can provide a better user experience by allowing applications to run faster and more smoothly, without the need for expensive hardware.
Challenges and Considerations
While both cloud computing and full stack development offer a plethora of advantages, there are some challenges and considerations to keep in mind when implementing these technologies. Firstly, full stack development can be time-consuming and require a wide range of technical skills. This can make it difficult for developers to keep up with the latest advancements and technologies. Additionally, integrating cloud computing into a full stack development process can also be a challenge, as the technology is constantly evolving and requires a significant investment in terms of time and resources.
Another consideration is choosing the right technology stack and cloud computing services for your organization. It is essential to assess your organization's needs, budget, and goals before making a decision. It's also important to ensure that the technology stack and cloud computing services you choose are compatible and can work seamlessly together.
Full Stack Development is a software development approach that covers all aspects of software development, including front-end development, back-end development, database management, and deployment. This approach enables developers to build and deploy complete software applications, from start to finish, without relying on others for assistance. In other words, Full Stack Developers are jack-of-all-trades, who have a deep understanding of all aspects of software development, from front-end design to back-end deployment.
The rise of Full Stack Development is a result of the rapidly evolving software development industry, which demands a more comprehensive approach to software development. Gone are the days when software development was a specialization that required different developers for the front-end design, back-end development, database management, and deployment. Today's fast-paced software development environment requires developers to have a broader understanding of all aspects of software development, to be able to quickly and efficiently build, deploy, and maintain software applications.
Summary
We have seen the different benefits that both Full Stack Development and Cloud Computing offer including improved collaboration and communication, increased flexibility and scalability, reduced costs, improved security, and better user experience. However, it's important to consider the challenges and weigh the benefits and considerations before implementing these technologies.
If you're looking to take your skills to the next level and become a Full Stack Developer, Skillslash's Full Stack Developer program is the perfect opportunity. The program provides comprehensive training in Full Stack Development, with a focus on practical hands-on learning. With a curriculum designed by industry experts and flexible online learning options, you'll acquire the skills you need to succeed in the tech industry. The program also provides you with a certificate of completion, making it easier for you to showcase your skills to potential employers.
So, if you are interested in building a career in data science, or business analytics, both the programs mentioned above are the perfect starting point. They provide students with the knowledge and skills they need to excel in today's data-driven world, and they are tailored to meet the demands of the job market.
Moreover, Skillslash also has in store, exclusive courses like System design course, Best Dsa course and Data Structures and Algorithms full Course to ensure aspirants of each domain have a great learning journey and a secure future in these fields. To find out how you can make a career in the IT and tech field with Skillslash, contact the student support team to know more about the course and institute.
https://skillslash.com/best-dsa-course
https://skillslash.com/best-data-structures-algorithms-course
https://skillslash.com/system-design-course
In this article, we'll dive into the world of both these domains, exploring the benefits and considerations of these technologies, and discussing why they are becoming increasingly important in today's tech landscape. Whether you're a tech professional or simply a tech enthusiast, you're sure to learn something new and thought-provoking as we dive into this exciting topic!
What is Full Stack Development?
Full Stack Development refers to the practice of developing both the front-end and back-end components of an application. Full Stack Developers possess a broad range of technical skills and knowledge, allowing them to develop, maintain and manage all aspects of an application.
To be a Full Stack Developer, you need to have a strong understanding of front-end technologies like HTML, CSS, and JavaScript, as well as back-end technologies such as servers, databases, and APIs. These technologies work together to create a seamless user experience, from the way a website looks and feels to the way it processes and stores data.
The front-end, or client-side, of an application is responsible for the visual design and user interaction. The back-end, or server-side, is responsible for processing data and communicating with the front-end. Full Stack Developers must have a good understanding of both sides of the application to ensure that they are working together smoothly.
What is Cloud Computing
Cloud Computing refers to the delivery of computing services—including servers, storage, databases, networking, software, analytics, and intelligence—over the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale.
There are three main categories of cloud computing services:
● Infrastructure as a Service (IaaS): provides virtualized computing resources over the internet. This includes virtual machines, storage, and networking.
● Platform as a Service (PaaS): provides a platform for developing, running, and managing applications and services.
● Software as a Service (SaaS): provides access to software applications over the internet, without the need for installation or maintenance.
One of the biggest advantages of cloud computing is its scalability. You can easily scale your resources up or down depending on your needs, without having to invest in additional hardware. This means that you can quickly respond to changes in demand, without having to worry about the underlying infrastructure.
Benefits of Full Stack Development and Cloud Computing
These 2 fields are two of the most important technology trends in today's tech landscape. When combined, they bring a multitude of benefits that can enhance the development process, improve user experience, and save costs. Let's dive into some of the key benefits of cloud computing and full stack development.
A. Improved Collaboration and Communication
One of the biggest benefits of is improved collaboration and communication. With Full Stack Development, front-end and back-end developers work together seamlessly, leading to improved collaboration among teams. This also leads to better communication between developers and clients, as everyone is on the same page in terms of the development process.
B. Increased Flexibility and Scalability
Full Stack Development allows developers to be flexible in their development processes, allowing them to quickly pivot and make changes as needed. This is especially important in today's fast-paced tech landscape where projects can change quickly.
Cloud Computing also provides scalability, as applications can be easily scaled up or down based on the needs of the project. This means that as the demand for an application grows, it can be easily scaled to meet that demand, without having to worry about the costs associated with purchasing new hardware.
C. Reduced Costs
With cloud computing, organizations can reduce the costs of hardware and infrastructure, as well as the costs associated with maintenance and updates. This is because it allows organizations to pay for only what they use, rather than having to purchase and maintain their own hardware.
D. Improved Security
Security is a major concern for organizations in today's tech landscape, and full stack development and cloud computing can help improve security measures. Cloud computing provides enhanced security measures, such as encryption and data backup, to protect sensitive information. Further, full stack development can improve data protection, as developers can build security measures at every stage of the development process.
E. Better User Experience
Both these tech fields can also lead to a better user experience. With full stack development, developers can create applications with enhanced functionality, which can greatly improve the user experience. Also, cloud computing can provide a better user experience by allowing applications to run faster and more smoothly, without the need for expensive hardware.
Challenges and Considerations
While both cloud computing and full stack development offer a plethora of advantages, there are some challenges and considerations to keep in mind when implementing these technologies. Firstly, full stack development can be time-consuming and require a wide range of technical skills. This can make it difficult for developers to keep up with the latest advancements and technologies. Additionally, integrating cloud computing into a full stack development process can also be a challenge, as the technology is constantly evolving and requires a significant investment in terms of time and resources.
Another consideration is choosing the right technology stack and cloud computing services for your organization. It is essential to assess your organization's needs, budget, and goals before making a decision. It's also important to ensure that the technology stack and cloud computing services you choose are compatible and can work seamlessly together.
Full Stack Development is a software development approach that covers all aspects of software development, including front-end development, back-end development, database management, and deployment. This approach enables developers to build and deploy complete software applications, from start to finish, without relying on others for assistance. In other words, Full Stack Developers are jack-of-all-trades, who have a deep understanding of all aspects of software development, from front-end design to back-end deployment.
The rise of Full Stack Development is a result of the rapidly evolving software development industry, which demands a more comprehensive approach to software development. Gone are the days when software development was a specialization that required different developers for the front-end design, back-end development, database management, and deployment. Today's fast-paced software development environment requires developers to have a broader understanding of all aspects of software development, to be able to quickly and efficiently build, deploy, and maintain software applications.
Summary
We have seen the different benefits that both Full Stack Development and Cloud Computing offer including improved collaboration and communication, increased flexibility and scalability, reduced costs, improved security, and better user experience. However, it's important to consider the challenges and weigh the benefits and considerations before implementing these technologies.
If you're looking to take your skills to the next level and become a Full Stack Developer, Skillslash's Full Stack Developer program is the perfect opportunity. The program provides comprehensive training in Full Stack Development, with a focus on practical hands-on learning. With a curriculum designed by industry experts and flexible online learning options, you'll acquire the skills you need to succeed in the tech industry. The program also provides you with a certificate of completion, making it easier for you to showcase your skills to potential employers.
So, if you are interested in building a career in data science, or business analytics, both the programs mentioned above are the perfect starting point. They provide students with the knowledge and skills they need to excel in today's data-driven world, and they are tailored to meet the demands of the job market.
Moreover, Skillslash also has in store, exclusive courses like System design course, Best Dsa course and Data Structures and Algorithms full Course to ensure aspirants of each domain have a great learning journey and a secure future in these fields. To find out how you can make a career in the IT and tech field with Skillslash, contact the student support team to know more about the course and institute.
https://skillslash.com/best-dsa-course
https://skillslash.com/best-data-structures-algorithms-course
https://skillslash.com/system-design-course
 |
Alexa Guillen
Oct 27, 2020
|
Death March Kara Hajimaru Isekai Kyōsōkyoku (デスマーチからはじまる異世界狂想曲 Desu Māchi Kara Hajimaru Isekai Kyōsōkyoku?), conocido como Death March to a Parallel World Rhapsody y comúnmente abreviado como DeathMa, es una serie de novelas ligeras japonesas escritas por Hiro Ainana e ilustradas por Shri. El primer volumen fue publicado en marzo de 2014. Una adaptación a manga por Ayamegumu fue hecha en Age Premium hasta que cesó la publicación, y fue entonces transferido a Monthly Dragon Age. Las dos novelas ligeras y la adaptación a manga han sido licenciadas para su publicación en Norteamérica por Yen Press. Una adaptación al anime producida por el estudio Silver Link y Connect se estrenó el 11 de enero de 2018.
Ichirō Suzuki es un programador que iba a tomar una siesta y de alguna manera despierta en el mundo que estaba editando antes de dormir, donde ve su nuevo nombre: Satou Pendragon. Al activar una habilidad que venia predeterminadamente, visualiza un grupo de hombres con forma de lagarto no muy lejos de su posición. Para sobrevivir, Satou utiliza la habilidad de regalo Lluvia de estrellas o Ducha de Meteoros, donde al aniquilar a todos los enemigos sube hasta el nivel 310 y se vuelve muy rico. Satou decide esconder su nivel y vivir pacíficamente conociendo personas nuevas. Aun así, desarrollos en la historia del juego, como el regreso de un rey de demonio, causan un inconveniente a los planes de Satou.
SE DICE Q MUY PRONTO 🔜 HABRÁ UNA SEGUNDA TEMPORADA PERO AÚN NO ESTÁ DEL TODO CONFIRMADA LA FECHA 📆 DE ESTRENO PERO IGUAL ESPERO QUE LES GUSTE 👌 ✌️
TAMBIÉN LES RECOMENDARÉ UNA APP PARA LEER MANGA
Ichirō Suzuki es un programador que iba a tomar una siesta y de alguna manera despierta en el mundo que estaba editando antes de dormir, donde ve su nuevo nombre: Satou Pendragon. Al activar una habilidad que venia predeterminadamente, visualiza un grupo de hombres con forma de lagarto no muy lejos de su posición. Para sobrevivir, Satou utiliza la habilidad de regalo Lluvia de estrellas o Ducha de Meteoros, donde al aniquilar a todos los enemigos sube hasta el nivel 310 y se vuelve muy rico. Satou decide esconder su nivel y vivir pacíficamente conociendo personas nuevas. Aun así, desarrollos en la historia del juego, como el regreso de un rey de demonio, causan un inconveniente a los planes de Satou.
SE DICE Q MUY PRONTO 🔜 HABRÁ UNA SEGUNDA TEMPORADA PERO AÚN NO ESTÁ DEL TODO CONFIRMADA LA FECHA 📆 DE ESTRENO PERO IGUAL ESPERO QUE LES GUSTE 👌 ✌️
TAMBIÉN LES RECOMENDARÉ UNA APP PARA LEER MANGA
|
|
gijap54623
Aug 08, 2022
|
Men's relaxed style is gradually taking over in the working environment (we're accusing you and those damn Adidas shoes, Zuckerberg), however that doesn't mean you ought to seem to be each and every other desk area bound drone at the workplace. Now is the right time to talk how to dress business relaxed.
Not business-y, but rather never too relaxed, the thought of a refined at this point agreeable office clothing standard is hazardously vague, without a few substantial borders. We've seen the ghastliness: men in sick fitting shirts, loose pants and undefined jackets, fizzling at office style and subliminally descending the company pecking order. It's not past the point of no return.
Peruse on for business easygoing style tips and the key pieces worth putting resources into.
Center Around Fit
The brilliant rule, in each custom fitted feeling of men's style, is buy clothing that fits you appropriately. Nothing obliterates an outfit - anything that the clothing standard and regardless of how costly the garments are - like an evil fitting coat, shirt or pant. The principal mysterious to looking brilliant is estimating accurately. Shoulders, midriff and a careful distance.
RELATED: Best Suit Brands For Men To Buy Right Now
Assemble Business Casual Basics
Whenever you've nailed the fit, you can fire developing your closet. Start with pieces that are not difficult to blend and match, so you can get the greatest value for your money, trading coats with jeans and shirts with ties for an alternate look every day.
After you've constructed a strong storeroom loaded with staples, you can begin getting more imaginative with surface, variety and example. Presently, read on for pieces you'll have to dress business easygoing.
The Business Casual Essentials
Assuming you construct your determination of basics cautiously, you'll have the option to accomplish greatest degrees of flexibility with least amounts of exertion (which is vital in the mornings and you haven't even had your espresso yet).
Overcoat
Starting things off with fit, the coat ought to sit square and cozy on the shoulders (no cresting) and be sliced thin through the sides and finish just underneath your butt. Sleeves finish a couple of centimeters over the thumb join to the shirt sleeve should be visible, just. See a designer to figure this out for you.
Covering winter, summer and each in the middle between, there are three coats you ought to consider. The first is an exemplary naval force coat, in a solitary bosom plan with pinnacle or score lapels. In light fleece, naval force is less stodgy than dark and is sufficiently dim to compliment your physical make-up, in a split second tiding up any look.
For cooler mornings, wear a dim tweed jacket. It's ideal from infusing surface (menswear's solution to adding revenue to a block tone with a bombastic print) and will function admirably with other warm hearted textures in your outfit, for example, cashmere pullover, silk sew tie and a chambray shirt.
At the point when the intensity is on, a beige unadulterated cotton or cloth mix coat will assist with keeping you cool in the workplace. Furthermore, its warm, natural tones will light up the workplace, swimming in an ocean of naval force coats, making you a business easygoing champion, justifiably. black shirt white blazer
Shirts
Sick fitting shirts are normal since we aren't all models and in extent from neck to abdomen. Once more, get the fit solidly in the shoulders first, Then, get across: the space between the neckline and the neck ought to fit two fingers serenely, and the shirt sleeve ought to meet at the thumb joint.
RELATED: The Best Casual Shirt Brands To Buy Right Now
In the event that your shoulders are expansive, search for a thin fit plan or consider getting darts; two basic straight creases put toward the rear of the shirt to secure in the swelling texture. This manual for dress shirt weaves will assist you with concluding which texture is best for your environment and clothing regulation. By and large, Oxford shirts are an attempted and tried traditional choice, and arrive in different varieties and examples.
Solids are clearly the least demanding to coordinate, so center at first around norms like white, light blue and pale pink, move into more splendid varieties and examples like stripes, checks or gingham renditions. Continuously remember that you ought to be more business than relaxed, so possibly wear a shirt on the off chance that the neckline can tolerate upping without a tie.
Pants
Because of a decline in suit coats in the workplace as of late, pants are a higher priority than at any other time. Along these lines, begin effective money management now.
Chinos in mid-weight cotton are your go-to decision for semi-formal workwear. Stay with exemplary tones - naval force and camel - and choose a fit that is thin yet not thin.
Pant isolates, again in a multipurpose variety, are the following stage up, wandering into dim or beige, particularly in winter in a rich wool or corduroy. Menswear's ongoing fixation on trimmed pants ought to be limited (put resources into a couple of max). On the off chance that you're after immortal stick to standard length, as patterns go back and forth.
At long last, pants are fitting - working environment allowing. Go for something else on the conventional finish of the denim range: mid-to-dim wash and positively no tears or weighty blurring. Office pants ought to likewise be thin, never thin.
Shoes
The dress shoe works of art are most secure with regards to your footwear. Loafers, Oxfords, Derbies, brogues and priest lashes will all look smart at the workplace, and will supplement each piece referenced above, permitting you to shape a total look when all united.
Easygoing Fridays might take into consideration a negligible, neat and tidy shoe to be worn to work, however once more, likewise with the jean-rule, check with your supervisor first.
RELATED: Best Sneaker Brands To Buy Right Now
For quality, calfskin is in every case better, adhering to dark, brown, oxblood and tan while picking a variety. In summer, try different things with variety and even softened cowhide. This aide - how to wear shaded dress shoes - will help.
The Optional Business Casual Extras
Assuming you truly need an outfit that says "I'm going directly to the top, better beginning getting out that corner office, ASAP," you're prepared to toss these discretionary business easygoing additional items in with the general mish-mash:
Polos
The polo shirt is bringing on the traditional shirt for easy business style. Coming in cotton piqué or the retro weave assortment, the neckline can be worn secured to the neck, for a spotless completion.
In any case, leave the main three buttons open and spread normally, joining a mid year twofold breasted coat and light shaded chinos (and loafers) to play off the going-to-work-could-be-occasion state of mind.
Weaves
On the off chance that you're the sort to wear bolder varieties, the sweater is an incredible clothing thing to give a generally exhausting work closet somewhat pop. Stay away from sweaters with insane examples, as well as anything with a thick-check (like link weave).
The right knitwear needs to sneak by a coat when required, yet be sufficiently significant to hold its own performance. The best come in block tones, a thin fit and sit at beltline length, with an unobtrusive ribbed sew and sleeve. Sweatshirts are an incredible coat supplanting and fair better with a tie, continuously leaving the last two buttons scattered.
Last Word: Accessorize
Taking these fundamental office things, mess with variety and print mixes and adding in or taking out conventional suit extremities for a casual look, that is supercharged.
Ultimately, with regards to extras, we say toning it down would be best. Add a cowhide folio to your wristwatch-ed hand, and get rid of the tie, adhering to the possibility of 'easygoing'. By knowing the guidelines, you can now twist them a tad, and not seem to be a bonehead. That is the means by which the Italians make it happen!
Business Casual For Men FAQ
Might you at any point wear a jacket for business relaxed?
Most certainly. Have something like three overcoats for your business easygoing closet - a light fleece in exemplary naval force tone, a dark tweed and a beige cotton or material mix jacket.
What sort of shirt to wear in a business easygoing set up?
Just wear a shirt with necklines that can bear upping regardless of whether you are not wearing a tie. For tones, go for solids like white, light blue and pink. You can likewise wear checked and striped shirts.
Is wearing pants suitable in the working environment?
Indeed, yet keep it formal with mid-to-dull wash denim. Since you are actually in your working environment, abstain from tears and weighty blurring. Additionally, ditch the thin pants and go for thin fit all things being equal.
Not business-y, but rather never too relaxed, the thought of a refined at this point agreeable office clothing standard is hazardously vague, without a few substantial borders. We've seen the ghastliness: men in sick fitting shirts, loose pants and undefined jackets, fizzling at office style and subliminally descending the company pecking order. It's not past the point of no return.
Peruse on for business easygoing style tips and the key pieces worth putting resources into.
Center Around Fit
The brilliant rule, in each custom fitted feeling of men's style, is buy clothing that fits you appropriately. Nothing obliterates an outfit - anything that the clothing standard and regardless of how costly the garments are - like an evil fitting coat, shirt or pant. The principal mysterious to looking brilliant is estimating accurately. Shoulders, midriff and a careful distance.
RELATED: Best Suit Brands For Men To Buy Right Now
Assemble Business Casual Basics
Whenever you've nailed the fit, you can fire developing your closet. Start with pieces that are not difficult to blend and match, so you can get the greatest value for your money, trading coats with jeans and shirts with ties for an alternate look every day.
After you've constructed a strong storeroom loaded with staples, you can begin getting more imaginative with surface, variety and example. Presently, read on for pieces you'll have to dress business easygoing.
The Business Casual Essentials
Assuming you construct your determination of basics cautiously, you'll have the option to accomplish greatest degrees of flexibility with least amounts of exertion (which is vital in the mornings and you haven't even had your espresso yet).
Overcoat
Starting things off with fit, the coat ought to sit square and cozy on the shoulders (no cresting) and be sliced thin through the sides and finish just underneath your butt. Sleeves finish a couple of centimeters over the thumb join to the shirt sleeve should be visible, just. See a designer to figure this out for you.
Covering winter, summer and each in the middle between, there are three coats you ought to consider. The first is an exemplary naval force coat, in a solitary bosom plan with pinnacle or score lapels. In light fleece, naval force is less stodgy than dark and is sufficiently dim to compliment your physical make-up, in a split second tiding up any look.
For cooler mornings, wear a dim tweed jacket. It's ideal from infusing surface (menswear's solution to adding revenue to a block tone with a bombastic print) and will function admirably with other warm hearted textures in your outfit, for example, cashmere pullover, silk sew tie and a chambray shirt.
At the point when the intensity is on, a beige unadulterated cotton or cloth mix coat will assist with keeping you cool in the workplace. Furthermore, its warm, natural tones will light up the workplace, swimming in an ocean of naval force coats, making you a business easygoing champion, justifiably. black shirt white blazer
Shirts
Sick fitting shirts are normal since we aren't all models and in extent from neck to abdomen. Once more, get the fit solidly in the shoulders first, Then, get across: the space between the neckline and the neck ought to fit two fingers serenely, and the shirt sleeve ought to meet at the thumb joint.
RELATED: The Best Casual Shirt Brands To Buy Right Now
In the event that your shoulders are expansive, search for a thin fit plan or consider getting darts; two basic straight creases put toward the rear of the shirt to secure in the swelling texture. This manual for dress shirt weaves will assist you with concluding which texture is best for your environment and clothing regulation. By and large, Oxford shirts are an attempted and tried traditional choice, and arrive in different varieties and examples.
Solids are clearly the least demanding to coordinate, so center at first around norms like white, light blue and pale pink, move into more splendid varieties and examples like stripes, checks or gingham renditions. Continuously remember that you ought to be more business than relaxed, so possibly wear a shirt on the off chance that the neckline can tolerate upping without a tie.
Pants
Because of a decline in suit coats in the workplace as of late, pants are a higher priority than at any other time. Along these lines, begin effective money management now.
Chinos in mid-weight cotton are your go-to decision for semi-formal workwear. Stay with exemplary tones - naval force and camel - and choose a fit that is thin yet not thin.
Pant isolates, again in a multipurpose variety, are the following stage up, wandering into dim or beige, particularly in winter in a rich wool or corduroy. Menswear's ongoing fixation on trimmed pants ought to be limited (put resources into a couple of max). On the off chance that you're after immortal stick to standard length, as patterns go back and forth.
At long last, pants are fitting - working environment allowing. Go for something else on the conventional finish of the denim range: mid-to-dim wash and positively no tears or weighty blurring. Office pants ought to likewise be thin, never thin.
Shoes
The dress shoe works of art are most secure with regards to your footwear. Loafers, Oxfords, Derbies, brogues and priest lashes will all look smart at the workplace, and will supplement each piece referenced above, permitting you to shape a total look when all united.
Easygoing Fridays might take into consideration a negligible, neat and tidy shoe to be worn to work, however once more, likewise with the jean-rule, check with your supervisor first.
RELATED: Best Sneaker Brands To Buy Right Now
For quality, calfskin is in every case better, adhering to dark, brown, oxblood and tan while picking a variety. In summer, try different things with variety and even softened cowhide. This aide - how to wear shaded dress shoes - will help.
The Optional Business Casual Extras
Assuming you truly need an outfit that says "I'm going directly to the top, better beginning getting out that corner office, ASAP," you're prepared to toss these discretionary business easygoing additional items in with the general mish-mash:
Polos
The polo shirt is bringing on the traditional shirt for easy business style. Coming in cotton piqué or the retro weave assortment, the neckline can be worn secured to the neck, for a spotless completion.
In any case, leave the main three buttons open and spread normally, joining a mid year twofold breasted coat and light shaded chinos (and loafers) to play off the going-to-work-could-be-occasion state of mind.
Weaves
On the off chance that you're the sort to wear bolder varieties, the sweater is an incredible clothing thing to give a generally exhausting work closet somewhat pop. Stay away from sweaters with insane examples, as well as anything with a thick-check (like link weave).
The right knitwear needs to sneak by a coat when required, yet be sufficiently significant to hold its own performance. The best come in block tones, a thin fit and sit at beltline length, with an unobtrusive ribbed sew and sleeve. Sweatshirts are an incredible coat supplanting and fair better with a tie, continuously leaving the last two buttons scattered.
Last Word: Accessorize
Taking these fundamental office things, mess with variety and print mixes and adding in or taking out conventional suit extremities for a casual look, that is supercharged.
Ultimately, with regards to extras, we say toning it down would be best. Add a cowhide folio to your wristwatch-ed hand, and get rid of the tie, adhering to the possibility of 'easygoing'. By knowing the guidelines, you can now twist them a tad, and not seem to be a bonehead. That is the means by which the Italians make it happen!
Business Casual For Men FAQ
Might you at any point wear a jacket for business relaxed?
Most certainly. Have something like three overcoats for your business easygoing closet - a light fleece in exemplary naval force tone, a dark tweed and a beige cotton or material mix jacket.
What sort of shirt to wear in a business easygoing set up?
Just wear a shirt with necklines that can bear upping regardless of whether you are not wearing a tie. For tones, go for solids like white, light blue and pink. You can likewise wear checked and striped shirts.
Is wearing pants suitable in the working environment?
Indeed, yet keep it formal with mid-to-dull wash denim. Since you are actually in your working environment, abstain from tears and weighty blurring. Additionally, ditch the thin pants and go for thin fit all things being equal.
|
|
nandi111
Dec 09, 2021
|
Elon Musk Hair Transplant, Today there is practically nobody who has not known about Elon Musk and the PayPal, Space X and TESLA marks that were made without anyone else. The virtuoso and devilish Elon Musk, whose subsequent stage is anxiously being trailed by the entire world, can be viewed as one of the 10 most significant people of the century. All that the present superhuman is keen on, with his silly, basic posts via web-based media and lovely lady friends, just as the developments he brought to the universe of science and business, transform into gold.
But is it genuine that our legend has had a hair relocate? We audit it with photographs for you.
The Story of Elon Musk and His Hair
When we take a gander at the adolescence and youth photographs of Elon Musk, whose facial elements and appeal are practically as old as, we can perceive how the thick hair suits his face. Anyway toward the finish of puberty, the diminishing of the hair that falls on the brow can be handily seen, regardless of whether there was no shedding.
Our youthful virtuoso, who began to lose hair toward the start of his twenties and afterwards diminished and lost in the bleeding edge of his hair, gives genuine going bald at 29 years old. (The year 2000)
Why did Elon Musk lose his hair?
The male body starts to create testosterone while still in the belly, and this creation proceeds until the finish of life. During immaturity, the testosterone chemical is changed over into a chemical called dihydrotestosterone (DHT) by a compound called 5-alpha-reductase. While DHT builds the hair development of the body, it is answerable for the shedding of the hair in the bushy region. This kind of balding is called Male Pattern Hair Loss and Androgenetic Alopecia (AGA). Since there is no DHT receptor in the hair situated in a specific region at the back, the hair here doesn't drop out. Hence, the hair in this space is utilized as a benefactor in hair transplantation.
Even if you are a super tech virtuoso, you can oppose partially against the hereditary qualities. So what did the fruitful business person who lost his hairdo do? Did he foster a remedy for hair sparseness and hush up about it? In all honesty, we don't think the appropriate response is yes. We are certain that Elon Musk, who is likewise a promoting master, would tell the entire world with regards to a technique to regrow non-existent hair. However, he didn't surrender he pick hair transplantation, which is the best strategy to bring back hair today.
Elon Musk and Hair Transplant
Our money manager, who was 32 years of age in 2003, had his first hair relocated. Before Elon's first hair relocation, there was Norwood 4-Norwood 5 degree going bald. It is objective to prescribe a two-phase activity to patients with this level of balding. At the point when the picture that seen after this activity is analyzed, we can see that the relocated hair number was not exceptionally high and the thickness was kept low. The skin can be effortlessly recognized among the hair in the bleeding edge that makes up the hairline, and the slim hair structure sticks out. At the point when the Smile Hair Clinic specialists analyzed these photos, they inferred that around 30 unions were relocated per cm2. Hair transplantation at this thickness might be planned to ensure the benefactor region. Be that as it may, this technique can be picked by the hair relocate specialist in tasks where there isn't sufficient giver region. Sadly, we don't know whether the specialist proposed this force or Elon himself mentioned it. All things considered, we can acknowledge that he change once more into his bygone times even with this low thickness result.
When we analyze the photographs of the renowned CEO, who turned 40 in every 2012, we can see that he isn't just keen on science, yet additionally centres around his public activity, as well. The bleeding edge of her hair has descended, the sides of the already vacant cutting edge are filled. At the point when we analyze the hair on the sides and front of Elon Musk, who has a tight hairline now, we can undoubtedly see that the volume of his recently relocated hair, which can't be harmed by testosterone, is a lot higher. Analyzing the photographs, Smile Hair Clinic specialists gauge that 50-55 unions for every cm2 were relocated this time. Inspecting the photographs, Smile Hair Clinic specialists gauge that 50-55 unions for every cm2 were put this time. Even though we imagine that the hairline has gotten a little tighter throughout the long term, our hair relocates specialists, who audit the photographs, are not altogether certain with regards to the third or fourth transfer. However, they don't see a huge diminishing in the thickness of the giver site.
एलोन मस्क हेयर ट्रांसप्लांट, आज व्यावहारिक रूप से कोई भी नहीं है जो एलोन मस्क और पेपाल, स्पेस एक्स और टेस्ला के निशान के बारे में नहीं जानता है जो किसी और के बिना बनाए गए थे । गुणी और शैतानी एलोन मस्क, जिनके बाद के चरण उत्सुकता से पूरी दुनिया से में देखा जा सकता है । वह सब जो वर्तमान अलौकिक वेब-आधारित मीडिया और प्यारी महिला मित्रों के माध्यम से अपने मूर्खतापूर्ण, बुनियादी पदों के साथ उत्सुक है, जैसे कि वह विज्ञान और व्यवसाय के ब्रह्मांड में लाए गए घटनाक्रम, सोने में बदल जाते हैं ।
लेकिन क्या यह वास्तविक है कि हमारी किंवदंती के बाल स्थानांतरित हो गए हैं? हम आपके लिए तस्वीरों के साथ इसका ऑडिट करते हैं ।
एलोन मस्क और उनके बालों की कहानी
जब हम एलोन मस्क की किशोरावस्था और युवा तस्वीरों में एक गैंडर लेते हैं, जिनके चेहरे के तत्व और अपील व्यावहारिक रूप से पुराने हैं, तो हम अनुभव कर सकते हैं कि घने बाल उसके चेहरे पर कैसे सूट करते हैं । वैसे भी यौवन के खत्म होने की ओर, भौंह पर गिरने वाले बालों का कम होना आसानी से देखा जा सकता है, भले ही कोई बहा न हो ।
हमारे युवा कलाप्रवीण व्यक्ति, जो अपने बिसवां दशा की शुरुआत की ओर बाल खोना शुरू कर दिया और बाद में कम हो गया और अपने बालों के खून बह रहा किनारे में खो गया, 29 साल की उम्र में वास्तविक गंजा हो गया । (वर्ष 2000)
एलोन मस्क ने अपने बाल क्यों खो दिए?
पुरुष शरीर पेट में रहते हुए भी टेस्टोस्टेरोन बनाना शुरू कर देता है, और यह निर्माण जीवन के अंत तक आगे बढ़ता है । अपरिपक्वता के दौरान, टेस्टोस्टेरोन रसायन को 5-अल्फा-रिडक्टेस नामक यौगिक द्वारा डायहाइड्रोटेस्टोस्टेरोन (डीएचटी) नामक रसायन में बदल दिया जाता है । जबकि डीएचटी शरीर के बालों के विकास का निर्माण करता है, यह जंगली क्षेत्र में बालों के बहा देने के लिए जवाबदेह है । बिना बाल के इस तरह पुरुष पैटर्न बालों के झड़ने और एंड्रोजेनिक खालित्य (आगा) कहा जाता है । चूंकि पीठ पर एक विशिष्ट क्षेत्र में स्थित बालों में कोई डीएचटी रिसेप्टर नहीं है, इसलिए यहां के बाल बाहर नहीं निकलते हैं । इसलिए, इस जगह में बाल बाल प्रत्यारोपण में एक दाता के रूप में उपयोग किया जाता है ।
But is it genuine that our legend has had a hair relocate? We audit it with photographs for you.
The Story of Elon Musk and His Hair
When we take a gander at the adolescence and youth photographs of Elon Musk, whose facial elements and appeal are practically as old as, we can perceive how the thick hair suits his face. Anyway toward the finish of puberty, the diminishing of the hair that falls on the brow can be handily seen, regardless of whether there was no shedding.
Our youthful virtuoso, who began to lose hair toward the start of his twenties and afterwards diminished and lost in the bleeding edge of his hair, gives genuine going bald at 29 years old. (The year 2000)
Why did Elon Musk lose his hair?
The male body starts to create testosterone while still in the belly, and this creation proceeds until the finish of life. During immaturity, the testosterone chemical is changed over into a chemical called dihydrotestosterone (DHT) by a compound called 5-alpha-reductase. While DHT builds the hair development of the body, it is answerable for the shedding of the hair in the bushy region. This kind of balding is called Male Pattern Hair Loss and Androgenetic Alopecia (AGA). Since there is no DHT receptor in the hair situated in a specific region at the back, the hair here doesn't drop out. Hence, the hair in this space is utilized as a benefactor in hair transplantation.
Even if you are a super tech virtuoso, you can oppose partially against the hereditary qualities. So what did the fruitful business person who lost his hairdo do? Did he foster a remedy for hair sparseness and hush up about it? In all honesty, we don't think the appropriate response is yes. We are certain that Elon Musk, who is likewise a promoting master, would tell the entire world with regards to a technique to regrow non-existent hair. However, he didn't surrender he pick hair transplantation, which is the best strategy to bring back hair today.
Elon Musk and Hair Transplant
Our money manager, who was 32 years of age in 2003, had his first hair relocated. Before Elon's first hair relocation, there was Norwood 4-Norwood 5 degree going bald. It is objective to prescribe a two-phase activity to patients with this level of balding. At the point when the picture that seen after this activity is analyzed, we can see that the relocated hair number was not exceptionally high and the thickness was kept low. The skin can be effortlessly recognized among the hair in the bleeding edge that makes up the hairline, and the slim hair structure sticks out. At the point when the Smile Hair Clinic specialists analyzed these photos, they inferred that around 30 unions were relocated per cm2. Hair transplantation at this thickness might be planned to ensure the benefactor region. Be that as it may, this technique can be picked by the hair relocate specialist in tasks where there isn't sufficient giver region. Sadly, we don't know whether the specialist proposed this force or Elon himself mentioned it. All things considered, we can acknowledge that he change once more into his bygone times even with this low thickness result.
When we analyze the photographs of the renowned CEO, who turned 40 in every 2012, we can see that he isn't just keen on science, yet additionally centres around his public activity, as well. The bleeding edge of her hair has descended, the sides of the already vacant cutting edge are filled. At the point when we analyze the hair on the sides and front of Elon Musk, who has a tight hairline now, we can undoubtedly see that the volume of his recently relocated hair, which can't be harmed by testosterone, is a lot higher. Analyzing the photographs, Smile Hair Clinic specialists gauge that 50-55 unions for every cm2 were relocated this time. Inspecting the photographs, Smile Hair Clinic specialists gauge that 50-55 unions for every cm2 were put this time. Even though we imagine that the hairline has gotten a little tighter throughout the long term, our hair relocates specialists, who audit the photographs, are not altogether certain with regards to the third or fourth transfer. However, they don't see a huge diminishing in the thickness of the giver site.
एलोन मस्क हेयर ट्रांसप्लांट, आज व्यावहारिक रूप से कोई भी नहीं है जो एलोन मस्क और पेपाल, स्पेस एक्स और टेस्ला के निशान के बारे में नहीं जानता है जो किसी और के बिना बनाए गए थे । गुणी और शैतानी एलोन मस्क, जिनके बाद के चरण उत्सुकता से पूरी दुनिया से में देखा जा सकता है । वह सब जो वर्तमान अलौकिक वेब-आधारित मीडिया और प्यारी महिला मित्रों के माध्यम से अपने मूर्खतापूर्ण, बुनियादी पदों के साथ उत्सुक है, जैसे कि वह विज्ञान और व्यवसाय के ब्रह्मांड में लाए गए घटनाक्रम, सोने में बदल जाते हैं ।
लेकिन क्या यह वास्तविक है कि हमारी किंवदंती के बाल स्थानांतरित हो गए हैं? हम आपके लिए तस्वीरों के साथ इसका ऑडिट करते हैं ।
एलोन मस्क और उनके बालों की कहानी
जब हम एलोन मस्क की किशोरावस्था और युवा तस्वीरों में एक गैंडर लेते हैं, जिनके चेहरे के तत्व और अपील व्यावहारिक रूप से पुराने हैं, तो हम अनुभव कर सकते हैं कि घने बाल उसके चेहरे पर कैसे सूट करते हैं । वैसे भी यौवन के खत्म होने की ओर, भौंह पर गिरने वाले बालों का कम होना आसानी से देखा जा सकता है, भले ही कोई बहा न हो ।
हमारे युवा कलाप्रवीण व्यक्ति, जो अपने बिसवां दशा की शुरुआत की ओर बाल खोना शुरू कर दिया और बाद में कम हो गया और अपने बालों के खून बह रहा किनारे में खो गया, 29 साल की उम्र में वास्तविक गंजा हो गया । (वर्ष 2000)
एलोन मस्क ने अपने बाल क्यों खो दिए?
पुरुष शरीर पेट में रहते हुए भी टेस्टोस्टेरोन बनाना शुरू कर देता है, और यह निर्माण जीवन के अंत तक आगे बढ़ता है । अपरिपक्वता के दौरान, टेस्टोस्टेरोन रसायन को 5-अल्फा-रिडक्टेस नामक यौगिक द्वारा डायहाइड्रोटेस्टोस्टेरोन (डीएचटी) नामक रसायन में बदल दिया जाता है । जबकि डीएचटी शरीर के बालों के विकास का निर्माण करता है, यह जंगली क्षेत्र में बालों के बहा देने के लिए जवाबदेह है । बिना बाल के इस तरह पुरुष पैटर्न बालों के झड़ने और एंड्रोजेनिक खालित्य (आगा) कहा जाता है । चूंकि पीठ पर एक विशिष्ट क्षेत्र में स्थित बालों में कोई डीएचटी रिसेप्टर नहीं है, इसलिए यहां के बाल बाहर नहीं निकलते हैं । इसलिए, इस जगह में बाल बाल प्रत्यारोपण में एक दाता के रूप में उपयोग किया जाता है ।
|
|
alvira
Jul 21, 2023
|
MCAFEE Customer Support NUMBER USA|HELP-2023*
The full rundown of the McAfee Client service Number parts is:
McAfee Venture Security Administrator
McAfee Occasion Beneficiary
McAfee Progressed Connection Motor
McAfee Venture Log Administrator
McAfee Venture Log Search
McAfee Application Information Screen
McAfee Direct Joined Stockpiling
McAfee Worldwide Danger Knowledge
These various modules channel input information from a few sources through to the Endeavor Security Supervisor.
How does MCAFEE Customer Support NUMBER USA|HELP-2023*respond?
McAfee Client assistance Number represents Security Data and Occasion The board. It is a blend of two danger recognition methodologies. Have based Interruption Location Frameworks (HIDSs) glance through log documents for indications of odd action. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The board (SEM) is a NIDS methodology. McAfee Client service Number is the blend of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. Assuming that the items in each voyaging parcel are scrambled, all the SEM framework needs to chip away at is the bundle header information. SEM can't think about occasions in that frame of mind on the organization and on isolated gadgets.
SIM can see examples of action across gadgets. In any case, SIM procedures produce improved results with more source information. As the info data for SIM is composed to logs, the best SIM results accompany the progression of time. A major issue of SIM is that it recognizes interruption everything considered - it isn't quick.
McAfee Client service Number joins the qualities of SIM and SEM. Indeed, even McAfee Client service Number , with its shifted strategies, can't hinder interruption. This is the second line of safeguard and is expected to flush out pernicious exercises that have figured out how to slip past edge and limit protections.
About McAfee
McAfee was made in 1987 as McAfee Partners. The organization became Intel Security Gathering in 2014 and afterward McAfee, LLC in 2017. McAfee was the principal maker of business antivirus programming and acquired early triumphs, making the business an appealing takeover target. Unusual organizer, John McAfee pulled out from the organization in 1994, selling his portions in general. After a progression of takeovers, the organization was purchased by Intel in 2014. McAfee was then turned out once more into a free organization in 2017 with Intel actually keeping a huge shareholding.
As programmer exercises become more modern, the conventional antivirus model became unfit to safeguard an IT framework completely. The idea of "interruption" in an IT framework includes a programmer acquiring passage into an organization and laying out a drawn out occupation, which is named an "High level Persevering Danger (Well-suited)."
McAfee has put resources into AI programming that utilizes simulated intelligence methods to distinguish odd action without expecting to allude to a data set of movement marks.
McAfee Endeavor Security Supervisor
The McAfee Endeavor Security Supervisor (ESM) is the principal module of McAfee Client assistance Number , incorporates the primary control center for the framework, and ties together every one of the information takes care of that logs authorities and traffic screens supply.
The fundamental perspective on the control center spotlights on occasions yet gadget sees are likewise available. The control center of the ESM permits admittance to look and insightful offices.
MCAFEE Customer Support NUMBER USA|HELP-2023* modules
While the Endeavor Security Chief is the center of the McAfee Client service Number framework, a great deal of the information handling work is performed beyond that unit.
McAfee Occasion Recipient
The McAfee Occasion Recipient is a parted framework for log assortment. A specialist lives on each checked gadget. It can store gathered information locally in the event that the organization is inaccessible. The focal assortment framework speaks with all specialists to get information from them.
The focal regulator goes about as a log server. It reformats got information into a standard design, empowering all records to be put away together. Related occasions are stamped so they can be gathered by scientific hunts from here on out. This is known as a log relationship.
McAfee Progressed Relationship Motor
The High level Relationship Motor (Expert) expands on crafted by the Occasion Beneficiary. It look through past log records to see whether recently documented log messages relating to an occasion that is as of now underway and has been distinguished by before messages.
The Pro checks new records so they can be integrated with more seasoned log messages. The recognized message bunch doesn't connect comparative records; rather it utilizes a standard framework that spots signs of the very occasion that shows itself through various activities in various areas.
McAfee Venture Log Administrator
The Venture Log Director (ELM) is a log document chief and its motivation is to give the obligatory log record the executives offices expected by security principles. It makes log records for approaching log messages both as a wellspring of information for the Security Occasion Chief and for information security principles revealing.
While norms require crude logs to be saved and be open, the Security Occasion Director is just keen on specific records that feature strange exercises, so some log messages will be copied and put away in various organizations. ELM can be arranged to utilize either nearby or far off storage spaces. The ELM is a discretionary module in the McAfee Client assistance Number framework. The Undertaking Security Supervisor can work without the presence of the Endeavor Log Chief.
McAfee Venture Log Search
McAfee Venture Log Search (ELS) depends on Elasticsearch. It is a part of the McAfee Client care Number framework yet it is likewise ready to fill in as an independent utility. This search office can work on the documents created by McAfee Progressed Connection Motor and the Venture Log Supervisor also analyze records of occasions and distinguish conceivable interruption or information robbery. The ELS is incorporated into the control center of the Endeavor Security Chief and is planned for impromptu inquiries and investigation.
McAfee Application Information Screen
The Application Information Screen (ADM) gives the SEM part of McAfee Client care Number . This apparatus works on live information and watches all traffic around the organization. The screen can investigate messages and PDFs, looking for inserted Trojans and perilous projects.
The screen works at the application layer, so it can recognize assaults that programmers split across bundles, expecting to trick conventional organization screens. The help works on a Range port, copying information streams instead of sitting inline. This eliminates the risk of presenting slack on the organization.
As well as searching for approaching assault endeavors, the ADM scans active traffic for information misfortune occasions and unapproved interchanges. All disclosures are evaluated in consistence with information assurance norms.
McAfee Direct Joined Stockpiling
McAfee Direct Joined Stockpiling serves the Endeavor Security Supervisor and the Undertaking Log Chief, giving a Strike regulator, reflected reserve, and IO multi-pathing.
McAfee Worldwide Danger Knowledge for ESM
All the Worldwide Danger Knowledge (GTI) feed is a center McAfee administration that upholds its security items. The GTI is made accessible in a configuration reasonable for the Venture Security Supervisor.
McAfee SIEM arrangement choices
The McAfee Endeavor Security Director is accessible in two configurations. The first is an adaptable cloud-based help, called ESM Cloud. This is likely the more available choice that most clients will select.
There is a free preliminary for ESM Cloud. The preliminary is as downloadable programming that sudden spikes in demand for a VM on-premises as opposed to get to the genuine cloud administration. The standard on-premises form of the Venture Security Chief is a machine. Potential clients who need to survey this framework ought to likewise download the virtual machine variant presented as a preliminary for ESM Cloud.
Dashboard
The control center of the ESM is gotten to through a standard internet browser whither it is being conveyed as a cloud administration or as a machine. The screens of the help involve the full width of the program window and don't save space for a menu. The menu slides in from the left on-request at the press of a button in the title bar of each screen.
McAfee Client care Number Audit and Options
McAfee is notable as a maker of hostile to infection programming. In any case, the organization needed to develop and present new IT assurance frameworks to remain on the lookout. The McAfee Client service Number is certainly not a solitary item. The fundamental component in the McAfee Client care Number family is called McAfee Venture Security Director.
The full rundown of the McAfee Client service Number parts is:
McAfee Endeavor Security Supervisor
McAfee Occasion Collector
McAfee Progressed Connection Motor
McAfee Endeavor Log Supervisor
McAfee Endeavor Log Search
McAfee Application Information Screen
McAfee Direct Connected Stockpiling
McAfee Worldwide Danger Insight
These various modules channel input information from a few sources through to the Undertaking Security Chief.
How does McAfee Client assistance Number respond?
McAfee Client service Number represents Security Data and Occasion The board. It is a blend of two danger location systems. Have based Interruption Recognition Frameworks (HIDSs) glance through log documents for indications of peculiar movement. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The executives (SEM) is a NIDS technique. McAfee Client assistance Number is the mix of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. In the event that the items in each voyaging parcel a
The full rundown of the McAfee Client service Number parts is:
McAfee Venture Security Administrator
McAfee Occasion Beneficiary
McAfee Progressed Connection Motor
McAfee Venture Log Administrator
McAfee Venture Log Search
McAfee Application Information Screen
McAfee Direct Joined Stockpiling
McAfee Worldwide Danger Knowledge
These various modules channel input information from a few sources through to the Endeavor Security Supervisor.
How does MCAFEE Customer Support NUMBER USA|HELP-2023*respond?
McAfee Client assistance Number represents Security Data and Occasion The board. It is a blend of two danger recognition methodologies. Have based Interruption Location Frameworks (HIDSs) glance through log documents for indications of odd action. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The board (SEM) is a NIDS methodology. McAfee Client service Number is the blend of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. Assuming that the items in each voyaging parcel are scrambled, all the SEM framework needs to chip away at is the bundle header information. SEM can't think about occasions in that frame of mind on the organization and on isolated gadgets.
SIM can see examples of action across gadgets. In any case, SIM procedures produce improved results with more source information. As the info data for SIM is composed to logs, the best SIM results accompany the progression of time. A major issue of SIM is that it recognizes interruption everything considered - it isn't quick.
McAfee Client service Number joins the qualities of SIM and SEM. Indeed, even McAfee Client service Number , with its shifted strategies, can't hinder interruption. This is the second line of safeguard and is expected to flush out pernicious exercises that have figured out how to slip past edge and limit protections.
About McAfee
McAfee was made in 1987 as McAfee Partners. The organization became Intel Security Gathering in 2014 and afterward McAfee, LLC in 2017. McAfee was the principal maker of business antivirus programming and acquired early triumphs, making the business an appealing takeover target. Unusual organizer, John McAfee pulled out from the organization in 1994, selling his portions in general. After a progression of takeovers, the organization was purchased by Intel in 2014. McAfee was then turned out once more into a free organization in 2017 with Intel actually keeping a huge shareholding.
As programmer exercises become more modern, the conventional antivirus model became unfit to safeguard an IT framework completely. The idea of "interruption" in an IT framework includes a programmer acquiring passage into an organization and laying out a drawn out occupation, which is named an "High level Persevering Danger (Well-suited)."
McAfee has put resources into AI programming that utilizes simulated intelligence methods to distinguish odd action without expecting to allude to a data set of movement marks.
McAfee Endeavor Security Supervisor
The McAfee Endeavor Security Supervisor (ESM) is the principal module of McAfee Client assistance Number , incorporates the primary control center for the framework, and ties together every one of the information takes care of that logs authorities and traffic screens supply.
The fundamental perspective on the control center spotlights on occasions yet gadget sees are likewise available. The control center of the ESM permits admittance to look and insightful offices.
MCAFEE Customer Support NUMBER USA|HELP-2023* modules
While the Endeavor Security Chief is the center of the McAfee Client service Number framework, a great deal of the information handling work is performed beyond that unit.
McAfee Occasion Recipient
The McAfee Occasion Recipient is a parted framework for log assortment. A specialist lives on each checked gadget. It can store gathered information locally in the event that the organization is inaccessible. The focal assortment framework speaks with all specialists to get information from them.
The focal regulator goes about as a log server. It reformats got information into a standard design, empowering all records to be put away together. Related occasions are stamped so they can be gathered by scientific hunts from here on out. This is known as a log relationship.
McAfee Progressed Relationship Motor
The High level Relationship Motor (Expert) expands on crafted by the Occasion Beneficiary. It look through past log records to see whether recently documented log messages relating to an occasion that is as of now underway and has been distinguished by before messages.
The Pro checks new records so they can be integrated with more seasoned log messages. The recognized message bunch doesn't connect comparative records; rather it utilizes a standard framework that spots signs of the very occasion that shows itself through various activities in various areas.
McAfee Venture Log Administrator
The Venture Log Director (ELM) is a log document chief and its motivation is to give the obligatory log record the executives offices expected by security principles. It makes log records for approaching log messages both as a wellspring of information for the Security Occasion Chief and for information security principles revealing.
While norms require crude logs to be saved and be open, the Security Occasion Director is just keen on specific records that feature strange exercises, so some log messages will be copied and put away in various organizations. ELM can be arranged to utilize either nearby or far off storage spaces. The ELM is a discretionary module in the McAfee Client assistance Number framework. The Undertaking Security Supervisor can work without the presence of the Endeavor Log Chief.
McAfee Venture Log Search
McAfee Venture Log Search (ELS) depends on Elasticsearch. It is a part of the McAfee Client care Number framework yet it is likewise ready to fill in as an independent utility. This search office can work on the documents created by McAfee Progressed Connection Motor and the Venture Log Supervisor also analyze records of occasions and distinguish conceivable interruption or information robbery. The ELS is incorporated into the control center of the Endeavor Security Chief and is planned for impromptu inquiries and investigation.
McAfee Application Information Screen
The Application Information Screen (ADM) gives the SEM part of McAfee Client care Number . This apparatus works on live information and watches all traffic around the organization. The screen can investigate messages and PDFs, looking for inserted Trojans and perilous projects.
The screen works at the application layer, so it can recognize assaults that programmers split across bundles, expecting to trick conventional organization screens. The help works on a Range port, copying information streams instead of sitting inline. This eliminates the risk of presenting slack on the organization.
As well as searching for approaching assault endeavors, the ADM scans active traffic for information misfortune occasions and unapproved interchanges. All disclosures are evaluated in consistence with information assurance norms.
McAfee Direct Joined Stockpiling
McAfee Direct Joined Stockpiling serves the Endeavor Security Supervisor and the Undertaking Log Chief, giving a Strike regulator, reflected reserve, and IO multi-pathing.
McAfee Worldwide Danger Knowledge for ESM
All the Worldwide Danger Knowledge (GTI) feed is a center McAfee administration that upholds its security items. The GTI is made accessible in a configuration reasonable for the Venture Security Supervisor.
McAfee SIEM arrangement choices
The McAfee Endeavor Security Director is accessible in two configurations. The first is an adaptable cloud-based help, called ESM Cloud. This is likely the more available choice that most clients will select.
There is a free preliminary for ESM Cloud. The preliminary is as downloadable programming that sudden spikes in demand for a VM on-premises as opposed to get to the genuine cloud administration. The standard on-premises form of the Venture Security Chief is a machine. Potential clients who need to survey this framework ought to likewise download the virtual machine variant presented as a preliminary for ESM Cloud.
Dashboard
The control center of the ESM is gotten to through a standard internet browser whither it is being conveyed as a cloud administration or as a machine. The screens of the help involve the full width of the program window and don't save space for a menu. The menu slides in from the left on-request at the press of a button in the title bar of each screen.
McAfee Client care Number Audit and Options
McAfee is notable as a maker of hostile to infection programming. In any case, the organization needed to develop and present new IT assurance frameworks to remain on the lookout. The McAfee Client service Number is certainly not a solitary item. The fundamental component in the McAfee Client care Number family is called McAfee Venture Security Director.
The full rundown of the McAfee Client service Number parts is:
McAfee Endeavor Security Supervisor
McAfee Occasion Collector
McAfee Progressed Connection Motor
McAfee Endeavor Log Supervisor
McAfee Endeavor Log Search
McAfee Application Information Screen
McAfee Direct Connected Stockpiling
McAfee Worldwide Danger Insight
These various modules channel input information from a few sources through to the Undertaking Security Chief.
How does McAfee Client assistance Number respond?
McAfee Client service Number represents Security Data and Occasion The board. It is a blend of two danger location systems. Have based Interruption Recognition Frameworks (HIDSs) glance through log documents for indications of peculiar movement. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The executives (SEM) is a NIDS technique. McAfee Client assistance Number is the mix of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. In the event that the items in each voyaging parcel a

|
|
alvira
Jul 21, 2023
|
MCAFEE Customer Support NUMBER USA|HELP-2023*
The full rundown of the McAfee Client service Number parts is:
McAfee Venture Security Administrator
McAfee Occasion Beneficiary
McAfee Progressed Connection Motor
McAfee Venture Log Administrator
McAfee Venture Log Search
McAfee Application Information Screen
McAfee Direct Joined Stockpiling
McAfee Worldwide Danger Knowledge
These various modules channel input information from a few sources through to the Endeavor Security Supervisor.
How does MCAFEE Customer Support NUMBER USA|HELP-2023*respond?
McAfee Client assistance Number represents Security Data and Occasion The board. It is a blend of two danger recognition methodologies. Have based Interruption Location Frameworks (HIDSs) glance through log documents for indications of odd action. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The board (SEM) is a NIDS methodology. McAfee Client service Number is the blend of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. Assuming that the items in each voyaging parcel are scrambled, all the SEM framework needs to chip away at is the bundle header information. SEM can't think about occasions in that frame of mind on the organization and on isolated gadgets.
SIM can see examples of action across gadgets. In any case, SIM procedures produce improved results with more source information. As the info data for SIM is composed to logs, the best SIM results accompany the progression of time. A major issue of SIM is that it recognizes interruption everything considered - it isn't quick.
McAfee Client service Number joins the qualities of SIM and SEM. Indeed, even McAfee Client service Number , with its shifted strategies, can't hinder interruption. This is the second line of safeguard and is expected to flush out pernicious exercises that have figured out how to slip past edge and limit protections.
About McAfee
McAfee was made in 1987 as McAfee Partners. The organization became Intel Security Gathering in 2014 and afterward McAfee, LLC in 2017. McAfee was the principal maker of business antivirus programming and acquired early triumphs, making the business an appealing takeover target. Unusual organizer, John McAfee pulled out from the organization in 1994, selling his portions in general. After a progression of takeovers, the organization was purchased by Intel in 2014. McAfee was then turned out once more into a free organization in 2017 with Intel actually keeping a huge shareholding.
As programmer exercises become more modern, the conventional antivirus model became unfit to safeguard an IT framework completely. The idea of "interruption" in an IT framework includes a programmer acquiring passage into an organization and laying out a drawn out occupation, which is named an "High level Persevering Danger (Well-suited)."
McAfee has put resources into AI programming that utilizes simulated intelligence methods to distinguish odd action without expecting to allude to a data set of movement marks.
McAfee Endeavor Security Supervisor
The McAfee Endeavor Security Supervisor (ESM) is the principal module of McAfee Client assistance Number , incorporates the primary control center for the framework, and ties together every one of the information takes care of that logs authorities and traffic screens supply.
The fundamental perspective on the control center spotlights on occasions yet gadget sees are likewise available. The control center of the ESM permits admittance to look and insightful offices.
MCAFEE Customer Support NUMBER USA|HELP-2023* modules
While the Endeavor Security Chief is the center of the McAfee Client service Number framework, a great deal of the information handling work is performed beyond that unit.
McAfee Occasion Recipient
The McAfee Occasion Recipient is a parted framework for log assortment. A specialist lives on each checked gadget. It can store gathered information locally in the event that the organization is inaccessible. The focal assortment framework speaks with all specialists to get information from them.
The focal regulator goes about as a log server. It reformats got information into a standard design, empowering all records to be put away together. Related occasions are stamped so they can be gathered by scientific hunts from here on out. This is known as a log relationship.
McAfee Progressed Relationship Motor
The High level Relationship Motor (Expert) expands on crafted by the Occasion Beneficiary. It look through past log records to see whether recently documented log messages relating to an occasion that is as of now underway and has been distinguished by before messages.
The Pro checks new records so they can be integrated with more seasoned log messages. The recognized message bunch doesn't connect comparative records; rather it utilizes a standard framework that spots signs of the very occasion that shows itself through various activities in various areas.
McAfee Venture Log Administrator
The Venture Log Director (ELM) is a log document chief and its motivation is to give the obligatory log record the executives offices expected by security principles. It makes log records for approaching log messages both as a wellspring of information for the Security Occasion Chief and for information security principles revealing.
While norms require crude logs to be saved and be open, the Security Occasion Director is just keen on specific records that feature strange exercises, so some log messages will be copied and put away in various organizations. ELM can be arranged to utilize either nearby or far off storage spaces. The ELM is a discretionary module in the McAfee Client assistance Number framework. The Undertaking Security Supervisor can work without the presence of the Endeavor Log Chief.
McAfee Venture Log Search
McAfee Venture Log Search (ELS) depends on Elasticsearch. It is a part of the McAfee Client care Number framework yet it is likewise ready to fill in as an independent utility. This search office can work on the documents created by McAfee Progressed Connection Motor and the Venture Log Supervisor also analyze records of occasions and distinguish conceivable interruption or information robbery. The ELS is incorporated into the control center of the Endeavor Security Chief and is planned for impromptu inquiries and investigation.
McAfee Application Information Screen
The Application Information Screen (ADM) gives the SEM part of McAfee Client care Number . This apparatus works on live information and watches all traffic around the organization. The screen can investigate messages and PDFs, looking for inserted Trojans and perilous projects.
The screen works at the application layer, so it can recognize assaults that programmers split across bundles, expecting to trick conventional organization screens. The help works on a Range port, copying information streams instead of sitting inline. This eliminates the risk of presenting slack on the organization.
As well as searching for approaching assault endeavors, the ADM scans active traffic for information misfortune occasions and unapproved interchanges. All disclosures are evaluated in consistence with information assurance norms.
McAfee Direct Joined Stockpiling
McAfee Direct Joined Stockpiling serves the Endeavor Security Supervisor and the Undertaking Log Chief, giving a Strike regulator, reflected reserve, and IO multi-pathing.
McAfee Worldwide Danger Knowledge for ESM
All the Worldwide Danger Knowledge (GTI) feed is a center McAfee administration that upholds its security items. The GTI is made accessible in a configuration reasonable for the Venture Security Supervisor.
McAfee SIEM arrangement choices
The McAfee Endeavor Security Director is accessible in two configurations. The first is an adaptable cloud-based help, called ESM Cloud. This is likely the more available choice that most clients will select.
There is a free preliminary for ESM Cloud. The preliminary is as downloadable programming that sudden spikes in demand for a VM on-premises as opposed to get to the genuine cloud administration. The standard on-premises form of the Venture Security Chief is a machine. Potential clients who need to survey this framework ought to likewise download the virtual machine variant presented as a preliminary for ESM Cloud.
Dashboard
The control center of the ESM is gotten to through a standard internet browser whither it is being conveyed as a cloud administration or as a machine. The screens of the help involve the full width of the program window and don't save space for a menu. The menu slides in from the left on-request at the press of a button in the title bar of each screen.
McAfee Client care Number Audit and Options
McAfee is notable as a maker of hostile to infection programming. In any case, the organization needed to develop and present new IT assurance frameworks to remain on the lookout. The McAfee Client service Number is certainly not a solitary item. The fundamental component in the McAfee Client care Number family is called McAfee Venture Security Director.
The full rundown of the McAfee Client service Number parts is:
McAfee Endeavor Security Supervisor
McAfee Occasion Collector
McAfee Progressed Connection Motor
McAfee Endeavor Log Supervisor
McAfee Endeavor Log Search
McAfee Application Information Screen
McAfee Direct Connected Stockpiling
McAfee Worldwide Danger Insight
These various modules channel input information from a few sources through to the Undertaking Security Chief.
How does McAfee Client assistance Number respond?
McAfee Client service Number represents Security Data and Occasion The board. It is a blend of two danger location systems. Have based Interruption Recognition Frameworks (HIDSs) glance through log documents for indications of peculiar movement. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The executives (SEM) is a NIDS technique. McAfee Client assistance Number is the mix of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. In the event that the items in each voyaging parcel a
The full rundown of the McAfee Client service Number parts is:
McAfee Venture Security Administrator
McAfee Occasion Beneficiary
McAfee Progressed Connection Motor
McAfee Venture Log Administrator
McAfee Venture Log Search
McAfee Application Information Screen
McAfee Direct Joined Stockpiling
McAfee Worldwide Danger Knowledge
These various modules channel input information from a few sources through to the Endeavor Security Supervisor.
How does MCAFEE Customer Support NUMBER USA|HELP-2023*respond?
McAfee Client assistance Number represents Security Data and Occasion The board. It is a blend of two danger recognition methodologies. Have based Interruption Location Frameworks (HIDSs) glance through log documents for indications of odd action. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The board (SEM) is a NIDS methodology. McAfee Client service Number is the blend of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. Assuming that the items in each voyaging parcel are scrambled, all the SEM framework needs to chip away at is the bundle header information. SEM can't think about occasions in that frame of mind on the organization and on isolated gadgets.
SIM can see examples of action across gadgets. In any case, SIM procedures produce improved results with more source information. As the info data for SIM is composed to logs, the best SIM results accompany the progression of time. A major issue of SIM is that it recognizes interruption everything considered - it isn't quick.
McAfee Client service Number joins the qualities of SIM and SEM. Indeed, even McAfee Client service Number , with its shifted strategies, can't hinder interruption. This is the second line of safeguard and is expected to flush out pernicious exercises that have figured out how to slip past edge and limit protections.
About McAfee
McAfee was made in 1987 as McAfee Partners. The organization became Intel Security Gathering in 2014 and afterward McAfee, LLC in 2017. McAfee was the principal maker of business antivirus programming and acquired early triumphs, making the business an appealing takeover target. Unusual organizer, John McAfee pulled out from the organization in 1994, selling his portions in general. After a progression of takeovers, the organization was purchased by Intel in 2014. McAfee was then turned out once more into a free organization in 2017 with Intel actually keeping a huge shareholding.
As programmer exercises become more modern, the conventional antivirus model became unfit to safeguard an IT framework completely. The idea of "interruption" in an IT framework includes a programmer acquiring passage into an organization and laying out a drawn out occupation, which is named an "High level Persevering Danger (Well-suited)."
McAfee has put resources into AI programming that utilizes simulated intelligence methods to distinguish odd action without expecting to allude to a data set of movement marks.
McAfee Endeavor Security Supervisor
The McAfee Endeavor Security Supervisor (ESM) is the principal module of McAfee Client assistance Number , incorporates the primary control center for the framework, and ties together every one of the information takes care of that logs authorities and traffic screens supply.
The fundamental perspective on the control center spotlights on occasions yet gadget sees are likewise available. The control center of the ESM permits admittance to look and insightful offices.
MCAFEE Customer Support NUMBER USA|HELP-2023* modules
While the Endeavor Security Chief is the center of the McAfee Client service Number framework, a great deal of the information handling work is performed beyond that unit.
McAfee Occasion Recipient
The McAfee Occasion Recipient is a parted framework for log assortment. A specialist lives on each checked gadget. It can store gathered information locally in the event that the organization is inaccessible. The focal assortment framework speaks with all specialists to get information from them.
The focal regulator goes about as a log server. It reformats got information into a standard design, empowering all records to be put away together. Related occasions are stamped so they can be gathered by scientific hunts from here on out. This is known as a log relationship.
McAfee Progressed Relationship Motor
The High level Relationship Motor (Expert) expands on crafted by the Occasion Beneficiary. It look through past log records to see whether recently documented log messages relating to an occasion that is as of now underway and has been distinguished by before messages.
The Pro checks new records so they can be integrated with more seasoned log messages. The recognized message bunch doesn't connect comparative records; rather it utilizes a standard framework that spots signs of the very occasion that shows itself through various activities in various areas.
McAfee Venture Log Administrator
The Venture Log Director (ELM) is a log document chief and its motivation is to give the obligatory log record the executives offices expected by security principles. It makes log records for approaching log messages both as a wellspring of information for the Security Occasion Chief and for information security principles revealing.
While norms require crude logs to be saved and be open, the Security Occasion Director is just keen on specific records that feature strange exercises, so some log messages will be copied and put away in various organizations. ELM can be arranged to utilize either nearby or far off storage spaces. The ELM is a discretionary module in the McAfee Client assistance Number framework. The Undertaking Security Supervisor can work without the presence of the Endeavor Log Chief.
McAfee Venture Log Search
McAfee Venture Log Search (ELS) depends on Elasticsearch. It is a part of the McAfee Client care Number framework yet it is likewise ready to fill in as an independent utility. This search office can work on the documents created by McAfee Progressed Connection Motor and the Venture Log Supervisor also analyze records of occasions and distinguish conceivable interruption or information robbery. The ELS is incorporated into the control center of the Endeavor Security Chief and is planned for impromptu inquiries and investigation.
McAfee Application Information Screen
The Application Information Screen (ADM) gives the SEM part of McAfee Client care Number . This apparatus works on live information and watches all traffic around the organization. The screen can investigate messages and PDFs, looking for inserted Trojans and perilous projects.
The screen works at the application layer, so it can recognize assaults that programmers split across bundles, expecting to trick conventional organization screens. The help works on a Range port, copying information streams instead of sitting inline. This eliminates the risk of presenting slack on the organization.
As well as searching for approaching assault endeavors, the ADM scans active traffic for information misfortune occasions and unapproved interchanges. All disclosures are evaluated in consistence with information assurance norms.
McAfee Direct Joined Stockpiling
McAfee Direct Joined Stockpiling serves the Endeavor Security Supervisor and the Undertaking Log Chief, giving a Strike regulator, reflected reserve, and IO multi-pathing.
McAfee Worldwide Danger Knowledge for ESM
All the Worldwide Danger Knowledge (GTI) feed is a center McAfee administration that upholds its security items. The GTI is made accessible in a configuration reasonable for the Venture Security Supervisor.
McAfee SIEM arrangement choices
The McAfee Endeavor Security Director is accessible in two configurations. The first is an adaptable cloud-based help, called ESM Cloud. This is likely the more available choice that most clients will select.
There is a free preliminary for ESM Cloud. The preliminary is as downloadable programming that sudden spikes in demand for a VM on-premises as opposed to get to the genuine cloud administration. The standard on-premises form of the Venture Security Chief is a machine. Potential clients who need to survey this framework ought to likewise download the virtual machine variant presented as a preliminary for ESM Cloud.
Dashboard
The control center of the ESM is gotten to through a standard internet browser whither it is being conveyed as a cloud administration or as a machine. The screens of the help involve the full width of the program window and don't save space for a menu. The menu slides in from the left on-request at the press of a button in the title bar of each screen.
McAfee Client care Number Audit and Options
McAfee is notable as a maker of hostile to infection programming. In any case, the organization needed to develop and present new IT assurance frameworks to remain on the lookout. The McAfee Client service Number is certainly not a solitary item. The fundamental component in the McAfee Client care Number family is called McAfee Venture Security Director.
The full rundown of the McAfee Client service Number parts is:
McAfee Endeavor Security Supervisor
McAfee Occasion Collector
McAfee Progressed Connection Motor
McAfee Endeavor Log Supervisor
McAfee Endeavor Log Search
McAfee Application Information Screen
McAfee Direct Connected Stockpiling
McAfee Worldwide Danger Insight
These various modules channel input information from a few sources through to the Undertaking Security Chief.
How does McAfee Client assistance Number respond?
McAfee Client service Number represents Security Data and Occasion The board. It is a blend of two danger location systems. Have based Interruption Recognition Frameworks (HIDSs) glance through log documents for indications of peculiar movement. Security Data The board (SIM) is a HIDS. Network-based Interruption Recognition Frameworks (NIDSs) watch network traffic to search for interruptions. Security Occasion The executives (SEM) is a NIDS technique. McAfee Client assistance Number is the mix of SIM and SEM.
The benefit of SEM is that it chips away at live information. In any case, network screens just work on one mark of the organization and watch all passing traffic. In the event that the items in each voyaging parcel a

 |
ZUMO TORWOLAN
Apr 18, 2021
|
hola alguien kieres ser mi amiga
animes vistos
-given
-beastars
-boku no hero
-banana fish
animes vistos
-given
-beastars
-boku no hero
-banana fish
|
Informe
Usted tiene algún problema o sugerencia, no dude en contactar con nosotros.
|
|
Transmitir
Enviar
@
Emoji
😀
😁
😂
😄
😆
😉
😊
😋
😎
😍
😘
🙂
😐
😏
😣
😯
😪
😫
😌
😜
😒
😔
😖
😤
😭
😱
😳
😵
😠
🤔
🤐
😴
😔
🤑
🤗
👻
💩
🙈
🙉
🙊
💪
👈
👉
👆
👇
🖐
👌
👏
🙏
🤝
👂
👃
👀
👅
👄
💋
💘
💖
💗
💔
❤
💤
💢
Clubs
Cargar página anterior

Cargar página siguiente
Amigos
Cargar página anterior

Cargar página siguiente
|
|
Imagen
Youtube
Vídeo
Enviar
|
|
Imagen
Youtube
Vídeo
Enviar
*El formato de url no es válido, verifique e intente nuevamente, por favor
Emoji
😀
😁
😂
😄
😆
😉
😊
😋
😎
😍
😘
🙂
😐
😏
😣
😯
😪
😫
😌
😜
😒
😔
😖
😤
😭
😱
😳
😵
😠
🤔
🤐
😴
😔
🤑
🤗
👻
💩
🙈
🙉
🙊
💪
👈
👉
👆
👇
🖐
👌
👏
🙏
🤝
👂
👃
👀
👅
👄
💋
💘
💖
💗
💔
❤
💤
💢
Clubs
Cargar página anterior

Cargar página siguiente
Amigos
Cargar página anterior

Cargar página siguiente
|
|
Imagen
Youtube
Vídeo
Enviar
Subir video
Empezar a subir
*El tipo de video debe ser MP4
Emoji
😀
😁
😂
😄
😆
😉
😊
😋
😎
😍
😘
🙂
😐
😏
😣
😯
😪
😫
😌
😜
😒
😔
😖
😤
😭
😱
😳
😵
😠
🤔
🤐
😴
😔
🤑
🤗
👻
💩
🙈
🙉
🙊
💪
👈
👉
👆
👇
🖐
👌
👏
🙏
🤝
👂
👃
👀
👅
👄
💋
💘
💖
💗
💔
❤
💤
💢
|
|
|





















